
EC-Council’s Certified Hacking Forensic Investigator (CHFI) is the only comprehensive ANSI accredited, lab-focused program in the market that gives organizations vendor-neutral training in digital forensics. CHFI provides its attendees with a firm grasp of digital forensics, presenting a detailed and methodological approach to digital forensics and evidence analysis that also pivots around Dark Web, IoT, and Cloud Forensics. The tools and techniques covered in this program will prepare the learner for conducting digital investigations using ground-breaking digital forensics technologies.
The program is designed for IT professionals involved with information system security, computer forensics, and incident response. It will help fortify the application knowledge in digital forensics for forensic analysts, cybercrime investigators, cyber defense forensic analysts, incident responders, information technology auditors, malware analysts, security consultants, and chief security officers. The program equips candidates with the necessary skills to proactively investigate complex security threats, allowing them to investigate, record, and report cybercrimes to prevent future attacks.
Student Shelter In Computers , EC-Council ATC Partner
EC-Council Partner Lahore Pakistan Offerís Low Cost Certification & Coaching / Training for Students &
Professionals

Computer Hacking Forensic Investigator CHFI
Training Course in Lahore Pakistan
Hacking
Forensic Investigation,
Information Security , Cyber Security Training & Certification
EC-Council Certification Courses Road-Map 2025-2026 (Download it)
https://www.eccouncil.org/wp-content/uploads/2023/02/Cyber-Handbook-Enterprise.pdf
Download CHFI Brochure

Computer Hacking Forensic Investigator CHFI
Training Course Outline
-
Computer Forensics in Today's World
-
Computer Forensics Investigation
Process
-
Searching and Seizing Computers
-
Digital Evidence
-
First Responder Procedures
-
Computer Forensics Lab
-
Understanding Hard Disks and File
Systems
-
Windows Forensics
-
Data Acquisition and Duplication
-
Recovering Deleted Files and Deleted
Partitions
-
Forensics Investigation Using
AccessData FTK
-
Forensics Investigation Using EnCase
-
Steganography and Image File Forensics
-
Application Password Crackers
-
Log Capturing and Event Correlation
-
Network Forensics, Investigating Logs
and Investigating Network Traffic
-
Investigating Wireless Attacks
-
Investigating Web Attacks
-
Tracking Emails and Investigating Email
Crimes
-
Mobile Forensics
-
Investigative Reports
-
Becoming an Expert Witness


CHFI is a skilled professional trained in the application of computer investigation and analysis techniques in the interests of determining potential legal evidence. CHFI professionals are aware of legally sound detailed methodological approach to computer forensics and evidence analysis. Computer Hacking Forensic Investigation (CHFI) is the process of detecting hacking attacks and properly extracting evidence to report the crime and conduct audits to prevent future attacks. Computer crime in today’s cyber world is on the rise. Computer Investigation techniques are being used by police, government and corporate entities globally and many of them turn to EC-Council for our Computer Hacking Forensic Investigator CHFI Certification Program.

Course Description
EC-Council releases the most advanced Computer
Hacking Forensic Investigator training in Lahore Pakistan program 312-49 in the
world. CHFI presents detailed methodological approach to computer forensics
and evidence analysis. It is a comprehensive course covering major forensic
investigation scenarios that enables students to acquire necessary hands-on
experience on various forensic investigation techniques and standard forensic
tools necessary to successfully carryout a computer forensic investigation
leading to prosecution of perpetrators. Battles between corporations,
governments, and countries are no longer fought using physical force. Cyber war
has begun and we can also see the consequences in our daily lives. With the
onset of sophisticated cyber-attacks, the need for advanced cyber security and
investigation training is a mandate in present day. If you or your organization
requires the knowledge or skills to identify, track, and prosecute the cyber
criminal, then this is the course for you. This course helps forensic
investigators to excel in incident handling and investigate various types of
security incidents such as data breaches, latest persistent security issues,
insider employee threats and intricate digital forensic circumstances and cases.
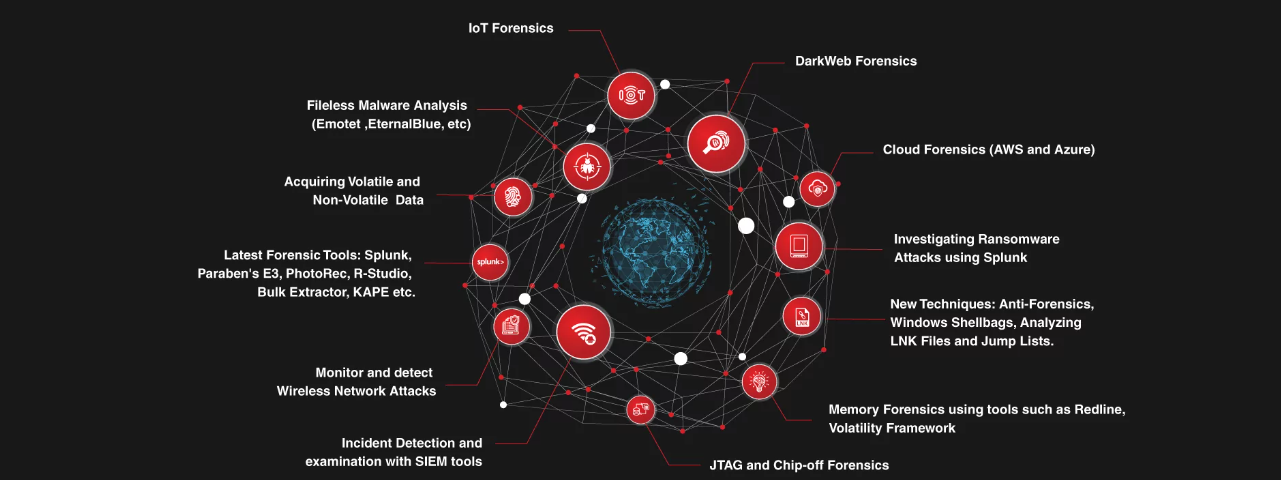
The Computer Hacking Forensic Investigator (CHFI) course training in Lahore Pakistan delivers the security discipline of digital forensics from a vendor-neutral perspective. CHFI is a comprehensive course covering major forensic investigation scenarios and enabling students to acquire necessary hands-on experience with various forensic investigation techniques and standard forensic tools necessary to successfully carry out a computer forensic investigation leading to the prosecution of perpetrators.
The CHFI certification gives participants (Law enforcement personnel, system administrators, security officers, defense and military personnel, legal professionals, bankers, security professionals, and anyone who is concerned about the integrity of the network infrastructure.) the necessary skills to perform an effective digital forensics investigation. CHFI presents a methodological approach to computer forensics including searching and seizing, chain-of-custody, acquisition, preservation, analysis and reporting of digital evidence.

As an Information Security Professional training course in Lahore Pakistan,
keeping up with new threats is hard enough, let alone keeping your employees
informed on new ways criminals are targeting them. Cyber Awareness Training strengthens
your organizationís security program by teaching your staff about current
criminal tactics so that your employees can avoid them. Employees learn on how
to protect themselves, and your organization, by participating in interactive
quizzes throughout the modules that reinforce the training materials. The
weakest link in an organizationís IT security plan is often its own employees.
Using social engineering, malicious emails, phishing, and other tactics,
criminals are often able to trick employees into disclosing private information
or bringing malware inside an organization. In recent surveys, nearly half of
all security, risk, and compliance officers have indicated that their own
employees are a greater risk than hackers or hacktivists. Cyber
awareness training can help your organization address this.

CHFI Hacking Forensic Investigation training course in Lahore Pakistan certifies individuals in the specific security discipline of computer forensics from a vendor-neutral perspective. The CHFI certification will fortify the application knowledge of law enforcement personnel, system administrators, security officers, defense and military personnel, legal professionals, bankers, security professionals, and anyone who is concerned about the integrity of the network infrastructure. Digital forensic practices stem from forensic science, the science of collecting and examining evidence or materials. Digital or computer forensics focuses on the digital domain including computer forensics, network forensics, and mobile forensics. As the cyber security profession evolves, organizations are learning the importance of employing digital forensic practices into their everyday activities. Cyber Crime Investigation Training in Lahore Pakistan.
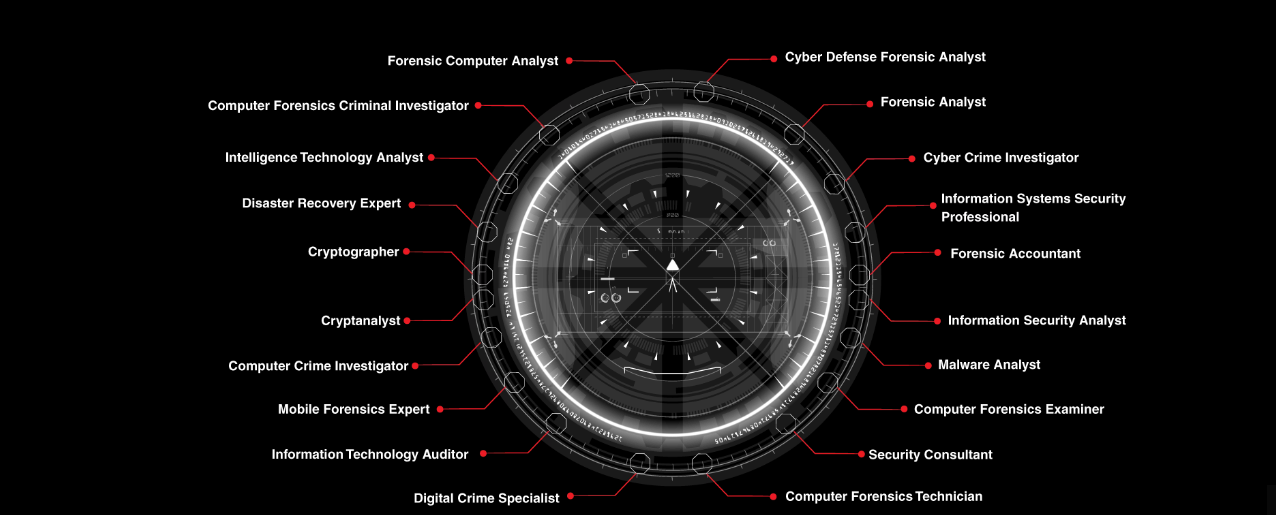
Computer hacking forensic investigation training course in Pakistan is the process of detecting hacking attacks and properly extracting evidence to report the crime and conduct audits to prevent future attacks. Computer crime in today’s cyber world is on the rise. Computer Investigation techniques are being used by police, government and corporate entities globally and many of them turn to EC-Council for our Computer Hacking Forensic Investigator CHFI Certification Program. EC-Council’s CHFI certifies individuals in the specific security discipline of computer forensics from a vendor-neutral perspective. The CHFI certification will fortify the application knowledge of law enforcement personnel, system administrators, security officers, defense and military personnel, legal professionals, bankers, security professionals, and anyone who is concerned about the integrity of the network infrastructure.

Hacking Forensic Investigation CHFI training Institute in Lahore Pakistan , Computer forensic training practices can help investigate attacks, system anomalies, or even help System administrators detect a problem by defining what is normal functional specifications and validating system information for irregular behaviors. In the event of a cyber-attack or incident, it is critical investigations be carried out in a manner that is forensically sound to preserve evidence in the event of a breach of the law. Far too many cyber-attacks are occurring across the globe where laws are clearly broken and due to improper or non-existent forensic investigations, the cyber criminals go either unidentified, undetected, or are simply not prosecuted. Cyber Security professionals who acquire a firm grasp on the principles of digital forensics can become invaluable members of Incident Handling and Incident response teams. The Computer Hacking Forensic Investigator course provides a strong baseline knowledge of key concepts and practices in the digital forensic domains relevant to today's organizations. CHFI provides its attendees a firm grasp on the domains of digital forensics. CHFI Training is for CID Crime Investigation Department Pakistan, FIA Federal Investigation Agency Pakistan, Pakistan Security Agencies, Pakistan Army, Pakistan Air Force, Pakistan Navy, Pakistan Intelligence Department, Cyber Crime Investigation Department, Information Security Organization, Pakistan Defense & Govt. Security Organization before they have to do CEH Ethical Hacking Training & Certification than they will be Eligible for Computer Hacking Forensic Investigation CHFI Training in Lahore Pakistan

|
 |
Mr. Ammar Jaffar Chairman PISA Pakistan Information Security Association, FIA & Cyber Security Selected! Mr. Abbas Shahid Baqir (Director Student Shelter In Computers) Become PISA Pakistan Information Security Association (Board Member, Coordinator Punjab & Lahore Chapter) gave responsibilities to work on Schools, Colleges, Universities, Education Sector, Govt. Organization, Banks, Private Sector & Misc. Organization on Cyber Security Awareness, Certified Ethical Hacking CEHv10 Awareness, Cyber Drills and COP Child Protection Law Projects. As PISA Coordinator Punjab, We Invited all Security Agencies, Organization, Companies, Colleges & Universities Students, Professors, Deans Organized Workshop / Seminars on Cyber Security, Ethical Hacker & Child Online Protection Programs and Invited us Student Shelter In Computers team we will work with them |

Designed &
Developed by Webmaster Abbas Shahid Baqir
Webmaster Feedback: stscomps@yahoo.com
All Rights
Reserved Copyright, 2010-2035 Student Shelter In Computers
ģ
















