|
 |
| Student
Shelter In Computers
Slogan
: Our Aim & Mission as a Organization to Promote Information
Technology , Cyber Security , Entrepreneurship Education into Young Generation
, Teach , Train & Employee them in Eduction Sector , Banks & Different
Industries and Bulid them Future Leaders. |
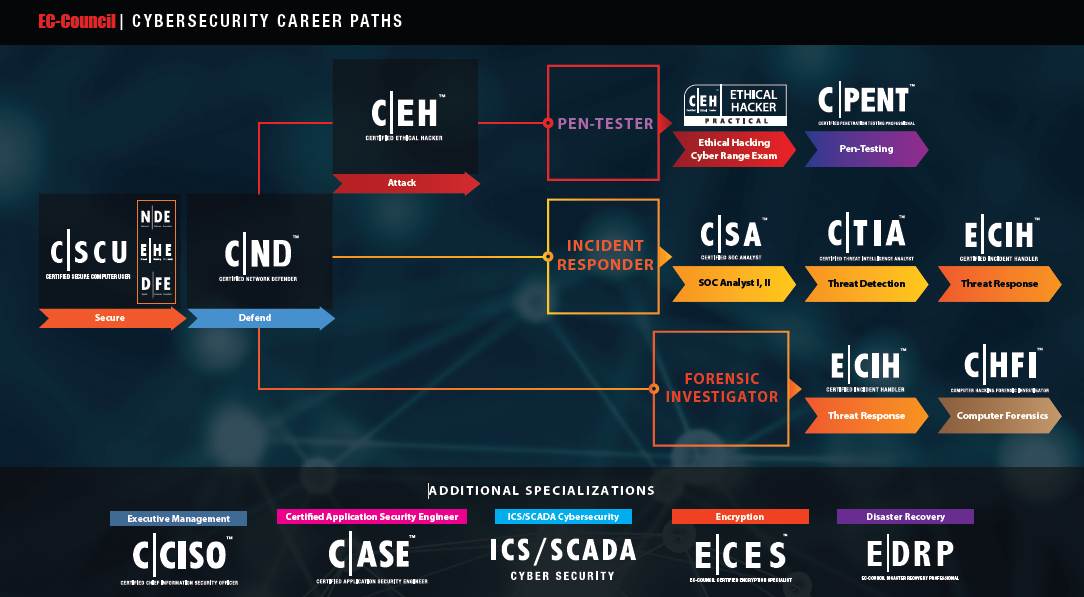
CEH
Ethical Hacking Training in Lahore & Cyber Security Trainings

Student Shelter In Computers , EC-Council Partner
in Pakistan
EC-Council ATC Partner
Lahore Pakistan Offer’s Low Cost Trainings for Students &
Professionals
EC-Council Certification Courses Road-Map 2025-2026 (Download it)
Download Advance Cyber Security Brochure

Student Shelter In Computers Training
is the
best Advance Cyber Secuirty Course in Lahore , IT CEH
training institute in
Lahore which
is offering CEH
Ethical Hacking Course in Lahore.
Cyber Security Course Near me , But before enrolling in CEH (Certified Ethical Hacker) course, stop for a
while! “What
you actually think and know about Ethical Hacking or CEH?” Besides
of all foolish myths about this course, this fact should be in your mind
that Ethical Hacking (also known as “Penetration
Testing”),
is a terminology used by computer systems and networks professionals, who
hacks the systems and pointing out the flaws and vulnerabilities in
computer system security. In today’s digital world, where all things,
operations and even humans are digitized, they are also facing serious
security attacks by
“Black Hat Hackers”
(terminology used for malicious and illegal hacker). To avoid these
attacks and finding out flaws in any system, services of
Ethical Hacker
also known as “White
Hat Hacker” is
highly needed and required. Cyber
Security training course in Lahore & CEH Ethical Hacking Training Course in Pakistan.
As an Information Security Professional training course in Lahore
Pakistan, keeping up with new threats is
hard enough, let alone keeping your employees informed on new ways
criminals are targeting them. Cyber Awareness Training strengthens your organization’s security program by teaching your staff
about current criminal tactics so that your employees can avoid them.
Employees learn on how to protect themselves, and your organization, by
participating in interactive quizzes throughout the modules that reinforce
the training materials. Cyber Security training Institute in Lahore Pakistan, Such professionals use the same skills and techniques hackers use to identify system vulnerabilities and access points for penetration, and to prevent unwanted access to network and information systems. Information Security Training in Pakistan, We offer Certified Ethical Hacker (CEH) is an intermediate-level credential offered by the International Council of E-Commerce Consultants (EC-Council). It's a must-have for IT professionals pursuing careers in ethical hacking. Cyber Secuirty Training Course in Lahore Pakistan

The weakest link in an organization’s IT security plan is often its own
employees. Using social engineering, malicious emails, phishing, and other
tactics, criminals are often able to trick employees into disclosing private
information or bringing malware inside an organization. In recent surveys,
nearly half of all security, risk, and compliance officers have indicated
that their own employees are a greater risk than hackers or hacktivists.
Cyber awareness training can help your organization address this.
We Provide Security from Facebook Hacking,
Twitter Hacking, Whatsapp Hacking, Instagram Hacking, Linkedin Hacking, Website Hacking, Email
account Hacking, Gmail Hacking , Yahoo account Hacking, Social Media account
Hacking. Our
responsibilities to
work on Schools, Colleges, Universities, Education Sector, Govt.
Organization, Banks, Private Sector & Misc. Organization on Cyber
Security Awareness, Ethical Hacking CEH Awareness, Cyber Drills in
Pakistan and COP Child Protection Law Projects. As PISA Pakistan
Information Security Coordinator Punjab, We Invited all Security
Agencies, Organization, Companies, Colleges & Universities Students,
Professors, Deans Organized Workshop / Seminars on Cyber Security, Ethical
Hacker & Child Online Protection. We offer Cyber Security Online Training in
Lahore Pakistan.
Ethical Hacking Training Classes in Pakistan

Ethical Hacking ,
Information Security , Artificial Intelliegnce , Cyber Security Trainings
EC-Council Certification Courses Road-Map 2025-2026 (Download it)
Download Advance Cyber Security Brochure
Cyber Security Training Course
Artifical Intelliegnce Training Course
NDE Network Defense Essentials
EHE Ethical Hacking Essentials
DFE Digital Forensics Essentials
IOT Security Essentials ISE
SOC Secuity Operation Center Essentials
TIE Threat Intelliegnce Essentials
NSC Network Security Course
ISC Information Security Course
CFC Computer Forensics Course
WSC Wireless Security Course
DevSecOps Essentials
CSE Cloud Security Essentials
CFF Computer Forensics Fundamentals
NDC Network Defense Course
Cyber Security and Artifical Intelliegnce Training Course
CEH Certified Ethical Hacking
CHFI Computer Hacking Forensic Investigation
ECSA EC-Council Certified
Security Analyst
AI Artifical Intelliegnce Training Course
Information Security Training Course
CPENT Certified Penetration Testing Professional
CCISO Certified Chief Information
Security Officer
CND Certified Network Defender
Certified SOC Analyst
Web Application Hacking Security
LPT License Penetration Testing
CSCU Secure Computer User
ECIH EC-Council Certified Incident
Handling
CTIA Certified Threat Intelligence Analyst
ECSS EC-Council Certified Security
Specialist
ECSP.net EC-Council Certified Secure Programmer
ECES EC-Council Certified Encryption
Specialist
EDRP EC-Council Disaster Recovery
Professional
ECVP EC-Council Certified VOIP
Professional
CNDA Certified Network Defense
Architect
Certified
Application Security Engineer Case.Net
Certified
Application Security Engineer Case Java
Digital Forensic Investigation
Hacking Training &
Certification

Ethical Hacking CEH training
course in Lahore Pakistan, CEH Ethical Hacking training class
in Lahore Pakistan , puts you in the driver's seat of a hands-on environment with a
systematic process. Here, you will be exposed to an entirely different way
of achieving optimal information security posture in their organization; by
hacking it! You will scan, test, hack and secure your own systems. You will
be taught the five phases of ethical hacking and thought how you can
approach your target and succeed at breaking in every time! The five phases
include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and
covering your tracks. Underground Hacking Tools , The hacking tools and techniques in each of these five phases are provided
in detail in an encyclopedic approach to help you identify when an attack
has been used against your own targets. Why then is this training called the Certified Ethical Hacker Course? This is because by using the same
techniques as the bad guys, you can assess the security posture of an
organization with the same approach these malicious hackers use, identify
weaknesses and fix the problems before they are identified by the enemy,
causing what could potentially be a catastrophic damage to your respective
organization. Hacking Training in Lahore Pakistan.
Ethical Hacking CEH Training in Lahore Pakistan

CEH Ethical Hacking
training Institute in Lahore Pakistan. We live in an age where attacks are all susceptible and come
from anyplace at any time and we never know how skilled, well-funded, or
persistent the threat will be. Throughout the CEH course, you will be
immersed in a hacker's mindset, evaluating not just logical, but physical
security. Exploring every possible point of entry to find the weakest link
in an organization. From the end user, the secretary, the CEO, misconfigurations,
vulnerable times during migrations even information left in the dumpster. Hackers are innovators
and constantly find new ways to attack information systems and exploit
system vulnerabilities. Savvy businesses proactively protect their
information systems by engaging the services and expertise of IT
professionals skilled in beating hackers at their own game (often called "white hat hackers" or simply "white hats"). Hacking
Training in Lahore Pakistan
Cyber Security training Institute in Lahore Pakistan, Such professionals use the same
skills and techniques hackers use to identify system vulnerabilities and
access points for penetration, and to prevent unwanted access to network and
information systems. Information Security Training in Pakistan, We offer Certified Ethical Hacker (CEH) is an
intermediate-level credential offered by the International Council of
E-Commerce Consultants (EC-Council). It's a must-have for IT professionals
pursuing careers in ethical hacking. Advance Cyber Security training course in Lahore Pakistan , CEH credential holders possess skills
and knowledge on hacking practices in areas such as foot printing and
reconnaissance, scanning networks, enumeration, system hacking, Trojans,
worms and viruses, sniffers, denial-of-service attacks, social engineering,
session hijacking, hacking web servers, wireless networks and web
applications, SQL injection, cryptography, penetration testing, evading IDS,
firewalls, and honey pots. Kali Linux Backtrack Operating System training
in Lahore Pakistan.
Ethical Hacking Training in Lahore Pakistan

What is the Role of AI in Cybersecurity?
Artificial Intelligence Course in Lahore Pakistan By Student Shelter In Computers. Before AI, conventional systems were less efficient in detecting and tackling unknown attacks, resulting in misleading outputs that proved hazardous to an organization’s security framework. However, the traditional approach saw a significant advancement with AI in addressing these challenges and delivering result-driven outcomes. Nowadays, AI cybersecurity solutions are seen as a driving force, owing to their capability to navigate threats in advance and suggest solutions to gain the upper hand over cybercriminals.
Artificial Intelligence and Cyber Security Course in Lahore. The rise of AI in the face of escalating threats has been instrumental in dealing with ever-evolving security challenges and developing strategies ahead of time. Organizations are now leveraging artificial intelligence and security along with professional expertise and new tools to protect their sensitive data and critical systems. AI-based solutions can help keep pace with emerging threats, detect and respond to new threats, and offer better cyber protection. However, like two sides of a coin, AI can be both a blessing and a curse. As a result, AI cybersecurity has become essential in safeguarding modern digital infrastructures. Artificial intelligence in security provides numerous benefits, particularly in how threats are detected and remediated. AI algorithms work on a proactive approach to analyzing data and identifying threats and malicious activities. Moreover, understanding the foundational elements of AI’s role in threat detection is essential for leveraging its full potential. AI Artificial Intelliegnce Training Course in Lahore Pakistan
What Are the Potential Threats Posed by AI in Cybersecurity
It is important to understand that while cybersecurity and AI together can enhance security, AI can also be exploited by threat actors. Hackers can leverage AI in several ways to pose significant threats to cybersecurity. AI can automate and enhance social engineering attacks, psychologically tricking individuals into revealing sensitive information and compromising data integrity and confidentiality. Deepfake technology, powered by AI, can manipulate visual or audio content to impersonate individuals, leading to identity theft, misinformation, and other malicious activities. Hackers can also manipulate AI algorithms by feeding them deceptive information, resulting in incorrect outputs and potentially undermining the effectiveness of AI-based security systems. Furthermore, attackers can develop targeted malware that can evade AI-based detection systems, making it harder for traditional security measures to identify and mitigate these threats. Let’s explore some potential risks associated with AI from the perspective of cybersecurity professionals worldwide. As AI continues to enhance various aspects of cybersecurity, it also finds applications in more specific areas, such as ethical hacking. One notable example is ChatGPT, which has been adapted to assist ethical hackers in numerous ways, showing how versatile and adaptable AI can be in addressing modern cybersecurity challenges. Artificial Intelliegnce and Cyber Security Training Course in Lahore Pakistan
|
 |
Mr. Ammar Jaffar Chairman PISA Pakistan Information Security Association, FIA & Cyber Security Selected! Mr. Abbas Shahid Baqir (Director Student Shelter In Computers) Become PISA Pakistan Information Security Association (Board Member, Coordinator Punjab & Lahore Chapter) gave responsibilities to work on Schools, Colleges, Universities, Education Sector, Govt. Organization, Banks, Private Sector & Misc. Organization on Cyber Security Awareness, Certified Ethical Hacking CEH Awareness, Cyber Drills, COP Child Protection Law Projects , Digital Forensic , Computer Forenisc Investigation. As PISA Coordinator Punjab, has provided cyber expertise to state and local law enforcement on investigations of crimes, including homicides, stalking, missing children, cyber-bullying, and internal affairs. As Certified Cyber Security instructor, we developed a cyber-based curriculum and has trained hundreds of law enforcement and private professionals in evidence acquisition, security policy and implementation, breach response and mitigation, hacker methodology, and employee Internet safety. We Invited all Security Agencies, Organization, Companies, Colleges & Universities Students, Professors, Deans Organized Workshop / Seminars on Cyber Security, Ethical Hacker & Child Online Protection Programs and Invited us Student Shelter In Computers team we will work with them |

CHFI Hacking Forensic Investigation
training
course in Lahore Pakistan certifies individuals in the specific security discipline of
computer forensics from a vendor-neutral perspective. The CHFI certification
will fortify the application knowledge of law enforcement personnel, system
administrators, security officers, defense and military personnel, legal
professionals, bankers, security professionals, and anyone who is concerned
about the integrity of the network infrastructure. Digital forensic practices
stem from forensic science, the science of collecting and examining evidence or
materials. Digital or computer forensics focuses on the digital domain including
computer forensics, network forensics, and mobile forensics. As the cyber
security profession evolves, organizations are learning the importance of
employing digital forensic practices into their everyday activities. Cyber
Crime Investigation Training in Lahore Pakistan.

Hacking Forensic Investigation CHFI training Institute in Lahore Pakistan ,
Computer
forensic training practices can help investigate attacks, system anomalies, or even help
System administrators detect a problem by defining what is normal functional
specifications and validating system information for irregular behaviors.
In the event of a cyber-attack or incident, it is critical investigations be
carried out in a manner that is forensically sound to preserve evidence in the
event of a breach of the law. Far too many cyber-attacks are occurring across
the globe where laws are clearly broken and due to improper or non-existent forensic investigations, the cyber criminals go either unidentified, undetected,
or are simply not prosecuted. Cyber Security professionals who acquire a firm grasp on the principles of digital forensics can become invaluable members of Incident Handling and
Incident response teams. The Computer Hacking Forensic Investigator course
provides a strong baseline knowledge of key concepts and practices in the
digital forensic domains relevant to today’s organizations. CHFI provides its
attendees a firm grasp on the domains of digital forensics. CHFI
Training is for CID Crime Investigation Department Pakistan, FIA Federal
Investigation Agency Pakistan, Pakistan Security Agencies, Pakistan Army,
Pakistan Air Force, Pakistan Navy, Pakistan Intelligence Department,
Cyber Crime Investigation Department, Information Security
Organization, Pakistan Defense & Govt. Security Organization before they have to do CEH Ethical Hacking Training & Certification than they will be Eligible for Computer Hacking Forensic Investigation
CHFI Training in Lahore Pakistan

Computer Hacking Forensic Iinvestigation in Lahore Pakistan is the process of detecting hacking attacks and properly extracting evidence to report the crime and conduct audits to prevent future attacks. Computer crime in today’s cyber world is on the rise. Computer Investigation techniques are being used by police, government, and corporate entities globally and many of them turn to EC-Council for our Digital Forensic Investigator CHFI Certification Program. Computer Security and Computer investigations in Pakistan are changing terms. More tools are invented daily for conducting Computer Investigations, be it computer crime, digital forensics, computer investigations, or even standard computer data recovery. The tools and techniques covered in EC-Council’s CHFI program will prepare the student to conduct computer investigations using ground-breaking digital forensics technologies.
Computer forensics is simply the application of computer investigation and analysis techniques in the interests of determining potential legal evidence. Evidence might be sought in a wide range of computer crime or misuse, including but not limited to theft of trade secrets, theft of or destruction of intellectual property, and fraud. CHFI investigators can draw on an array of methods for discovering data that resides in a computer system, or recovering deleted, encrypted, or damaged file information known as computer data recovery.
EC-Council’s CHFI certifies individuals in the specific security discipline of computer forensics from a vendor-neutral perspective. Our digital forensics certification will fortify the application knowledge of law enforcement personnel, system administrators, security officers, defense and military personnel, legal professionals, bankers, security professionals, and anyone who is concerned about the integrity of the network infrastructure.
Digital Computer forensics Investigation in Lahore Pakistan is the application of computer investigation and analysis techniques in the interests of determining potential legal evidence. Evidence might be sought in a wide range of computer crimes or misuse, including but not limited to; theft of trade secrets, theft of or destruction of intellectual property, and fraud. Computer forensic investigators can draw from an array of methods for discovering data that resides in a computer system, or recovering deleted, encrypted, or damaged file information. The CHFI course will give participants the necessary skills to identify an intruder’s footprints and to properly gather the necessary evidence to prosecute. Many of today’s top tools of the forensic trade will be taught during this course, including software, hardware and specialized techniques. It is no longer a matter of “will your organization be comprised (hacked)?” but, rather, “when?” Today’s battle between corporations, governments, and countries are no longer fought only in the typical arenas of boardrooms or battlefields using physical force. Now, the battlefield starts in the technical realm, which ties into most every facet of modern day life. If you or your organization requires the knowledge or skills to identify, track, and prosecute the cybercriminal, then this is the course for you.
Computer Hacking Forensic Investigation CHFI Training in Lahore Pakistan

Digital Forensics Investigations is a key component in Cyber Security. Many people hear the term forensics, or computer forensics, or digital forensics and instantly think that’s just for law enforcement, but the truth is, digital forensics has a key place on every cyber security team. In fact, without it, chances are your organization’s security posture and maturity will fail to see its full potential. Computer forensics is an evolving field that is always moving to match the changes in devices and how they are used for identifying, preserving, analyzing, and recovering data from computers and various digital media storage. Digital data are subjected to legal practices and guidelines when intended to serve as evidence in civil proceedings. Digital Computer Forensics Investigation training in Pakistan practices stem from forensic science, the science of collecting and examining evidence or materials. Digital or computer forensics focuses on the digital domain including computer forensics, network forensics, and mobile forensics. As the cyber security profession evolves, organizations are learning the importance of employing digital forensic practices into their everyday activities.
Computer Forensic training in Lahore Pakistan practices can help investigate attacks, system anomalies, or even help System administrators detect a problem by defining what is normal functional specifications and validating system information for irregular behaviors ares. In the event of a cyber-attack or incident, it is critical investigations be carried out in a manner that is forensically sound to preserve evidence in the event of a breach of the law. Far too many cyber-attacks are occurring across the globe where laws are clearly broken and due to improper or non-existent forensic investigations, the cyber criminals go either unidentified, undetected, or are simply not prosecuted. Cyber security professionals who acquire a firm grasp on the principles of digital forensics can become invaluable members of Incident Handling and Incident response teams. The Computer Forensic course provides a strong baseline knowledge of key concepts and practices in the digital forensic domains relevant to today’s organizations. CHFI provides its attendees with a firm grasp on the domains of digital forensics.
Digital Forensic Investigation CHFI Training in Lahore Pakistan

ECSA Security Analyst training
course in Lahore Pakistan , ECSA Security Analyst training Institute in Lahore Pakistan , Penetration testing course provides you with a real world hands-on
penetration testing experience and is a globally accepted hacking and
penetration testing class available that covers the testing of modern
infrastructures, operating systems and application environments while teaching
the students how to document and write a penetration testing report. This
makes the Certified Security Analyst "Pen Testing" certification a relevant
milestone toward achieving EC Council’s Licensed penetration Tester, which also
ingrains the learner in the business aspect of network penetration testing. The
Licensed Penetration Tester standardizes the knowledge base for network
penetration testing professionals by incorporating the best practices followed
by experienced experts in the field.
The objective of Certified
Security Analyst “pen testing” certification is to add value to experienced
Information security professionals by providing computer security training that
will help them analyze the outcomes of their Vulnerability Assessments. Network
Penetration Testing Training leads the learner into the advanced stages of
ethical hacking. ECSA
IT Security Training Course in Pakistan
Advanced Penetration Testing and Security Analyst ECSA training Institute in Lahore Pakistan,The Certified Security Analyst “pen testing” program is a computer security
certification designed to teach Information Security Professionals the advanced
uses of the available methodologies, tools and techniques expected from a
premier ethical hacking training and are required to perform comprehensive
information security pen tests. Students will learn how to design, secure and
test networks to protect your organization from the threats hackers and crackers
pose. By teaching the Licensed Penetration Tester, LPT methodology and ground
breaking techniques for security and penetration testing, this class will help
you perform the intensive assessments required to effectively identify and
mitigate risks to the security of your infrastructure. As students learn to
identify Information Security problems in this ethical hacking training
certification course, they also learn how to avoid and eliminate them, with the
class providing complete coverage of analysis and network security-testing
topics. Certified
Security Analyst ECSA Training in Lahore Pakistan

The Certified Penetration Testing Professional or CPENT training course in Lahore Pakistan , for short, re-writes the standards of penetration testing skill development. EC-Council’s Certified Penetration Tester (CPENT) program teaches you how to perform an effective penetration test in an enterprise network environment that must be attacked, exploited, evaded, and defended. If you have only been working in flat networks, CPENT’s live practice range will teach you to take your skills to the next level by teaching you how to pen test IoT systems, OT systems, how to write your own exploits, build your own tools, conduct advanced binaries exploitation, double pivot to access hidden networks, and also customize scripts/exploits to get into the innermost segments of the network.
The heart of the CPENT program is all about helping you master your pen testing skills by putting them to use on our live cyber ranges. The CPENT ranges were designed to be dynamic in order to give you a real-world training program, so just as targets and technology continue to change in live networks, both the CPENT practice and exam ranges will mimic this reality as our team of engineers continue to add targets and defenses throughout the CPENT course’s lifetime.
The Certified Penetration Testing Professional (CPENT) program by EC-Council was
created to prepare those that want to be recognized as elite penetration testing
professionals. Our training has been designed by the best in the industry and is
meant to push you to develop the kind of skill that you’ve been waiting to
acquire. LPT (Master) training (via CPENT) is not comfortable (and the exam is
even worse!), but filled with intense stress meant to elicit the best from you.
Those who prevail will have developed an instinctual response to real-world
penetration testing challenges. In this training program, you will learn
professional security and penetration testing skills. The course is designed to
show advanced concepts like advanced windows attacks, attacking IoT systems, and
writing exploits with advanced binary exploitation to go beyond flat networks.
You will learn to bypass a filtered network, pentest OT systems, access hidden
networks with pivoting, double pivot, escalate privilege, and evade defense
mechanisms.
The CPENT training in Pakistan range consists of entire network segments that replicate an enterprise network this is not a computer game simulation; this is an accurate representation of an enterprise network that will present the latest challenges to the pen tester. The benefit of hands on learning in a live cyber range is that candidates will encounter multiple layers of network segmentation, and the CPENT course will teach candidates how to navigate these layers, so that once access is gained in one segment, a candidate will know the latest pivoting techniques required to reach the next. However, that won’t be enough on its own as the targets and segments are progressive in nature, so once you get into one machine and or segment, the next one will challenge you even more!
CPENT Training Course in Lahore Pakistan

License Penetration Testing LPT training
course in Lahore Pakistan. The APT Advanced Penetration Testing
Training Course in Lahore Pakistan by EC-Council was created as the progression after the ECSA (Practical)
to prepare those that want to challenge the Licensed Penetration Tester (Master)
certification and be recognized as elite penetration testing professionals. Our
training has been designed by the best in the industry and meant to push you to
develop the kind of skill that you’ve been waiting to acquire. The exam will
require you to demonstrate mastery of deploying advanced pen testing techniques
and tools including multi-level pivoting, OS vulnerabilities exploits, SSH
tunneling, host-based application exploits, privilege escalation, web server
and web application exploitation such as arbitrary local and remote file upload,
SQL injection and parameter manipulation, etc – all in a real life scenario on
hardened machines, networks, and applications.
LPT (Master) training (via CPENT) is not comfortable (and the exam is
even worse!), but filled with intense stress meant to elicit the best from you.
Those who prevail will have developed an instinctual response to real-world
penetration testing challenges. In this training program, you will learn
professional security and penetration testing skills. The course is designed to
show advanced concepts like advanced windows attacks, attacking IoT systems, and
writing exploits with advanced binary exploitation to go beyond flat networks.
You will learn to bypass a filtered network, pentest OT systems, access hidden
networks with pivoting, double pivot, escalate privilege, and evade defense
mechanisms.
Penetration Testing training in Lahore Pakistan

LPT training Institute in Lahore Pakistan , LPT Master is not comfortable (and the exam is even worse!) , but filled with intense stress meant to illicit the best from you. Those who prevail will have developed an instinctual and intellectual response to real world penetration testing challenges. We want to bring out the best in you. Our aim is to push you to your limit while making you solve complex problems that actual penetration testers solve daily in the real world. For four punishing and long days, you will have to perform various tasks until it becomes second nature. This is the foundation of the program. This program is radically different from the ECSA. In the ECSA course, you are provided guidance on what machines to attack and an initial starting point. The course was created to provide you with advanced concepts that will help when it comes to attempting the LPT (Master) Certification exam. In this course you will learn professional security and penetration testing skills. In the Advanced Penetration Testing Course, you are presented with minimal network information along with a Scope of Work (SOW). The course is designed to show advanced concepts like scanning against defenses, pivoting between networks, deploying proxy chains, and using web shells. The last module of the course includes an SOW for each of the various networks we have created for the course. In the Advanced Penetration Testing Course, you are presented with minimal network information along with a Scope of Work (SOW). The course was created to provide you with advanced concepts that will help when it comes to attempting the LPT Master Certification exam. This, combined with the composition of various ranges, mimics a professional penetration test. Time is limited and you will be required to identify the attack surface followed by the weaknesses of the machines that are on the network.
License Penetration Testing LPT Training in Lahore Pakistan

The Advanced Penetration Testing APT course in Lahore Pakistan will teach you how to perform a professional security test as well as how to produce the next most important thing… the findings and the report! The ranges progress in difficulty and reflect an enterprise level architecture. There will be defenses to defeat and challenges to overcome. This is not your typical FLAT network! As the range levels increase you will encounter the top defenses of today and learn the latest evasion techniques.This program is meticulously designed to demonstrate the advanced concepts including that of scanning against defenses, pivoting between networks, deploying proxy chains and using web shells.The “virtual cyber ranges” bring 100% practicality into the training sessions and are designed to provide professional skills that demonstrate how professional pentesters determine the attack surface of targets within required time frames and complexities and gain access to the machines and escalate privileges.
The practical environment ranges progress in difficulty and reflect enterprise network architectures. This environment includes defenses and challenges which candidates of the LPT program must defeat and overcome. This is not done through a typical FLAT network! As candidates progress through the various range levels, each encounter will present the top defenses of today and they will learn the latest best practices, tips and tricks, and even evasion techniques.
Advanced Penetration Testing APT course in Pakistan , Penetration Testing is a legal, structured procedure to evaluate the security posture of an organization. This practice simulates an attack against the security infrastructure of the enterprise, such as its network, applications, and users, to identify the exploitable vulnerabilities. It determines the efficacy of the company’s security policies, controls, and strategies. To strengthen the system, penetration testers proactively analyse for design flaws, technical weaknesses, and other vulnerabilities. The results of the vulnerability assessment are then comprehensively documented for executive management and the company’s technical audience.
Advance Penetration Testing APT Training in Lahore Pakistan

CND Network Defender Training Course in Lahore Pakistan ,
Organizational focus on cyber defense is more important than ever as cyber
breaches have a far greater financial impact and can cause broad reputation
damage. You will learn how to protect, detect and respond to the network
attacks. You will learn network defense fundamentals, the application of network
security controls, protocols, perimeter appliances, secure IDS, VPN and firewall
configuration. You will then learn the intricacies of network traffic signature,
analysis and vulnerability scanning which will help you when you design greater
network security policies and successful incident response plans. These skills
will help you foster resiliency and continuity of operations during attacks.
Certified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led
comprehensive network security certification training program. It is a
skills-based, lab intensive program based on a job-task analysis and cyber
security education framework presented by the National Initiative of Cyber
security Education (NICE). The course has also been mapped to global job roles
and responsibilities and the Department of Defense (DoD) job roles for
system/network administrators. The course is designed and developed after
extensive market research and surveys.
There is no proper tactical network security training that is made
available for network administrators which provides them core network
security skills. Students enrolled in the Certified Network Defender course, will gain a detailed understanding and hands on ability to function in
real life situations involving network defense. They will gain the technical
depth required to actively design a secure network in your organization. This
program will be akin to learning math instead of just using a calculator. This
course gives you the fundamental understanding of the true construct of data
transfer, network technologies, software technologies so that you understand how
networks operate, understand what software is automating and how to analyze the
subject material.
The Certified Network Defender CND training Institute in Lahore Pakistan ,
(CND) certification program focuses on creating Network Administrators who are trained on protecting, detecting and responding
to the threats on the network. Network administrators are usually familiar with
network components, traffic, performance and utilization, network topology,
location of each system, security policy, etc. A CND will get the fundamental
understanding of the true construct of data transfer, network technologies,
software technologies so that the they understand how networks operate,
understand what software is automating and how to analyze the subject material.
In addition, network defense fundamentals, the application of network security
controls, protocols, perimeter appliances, secure IDS, VPN and firewall
configuration, intricacies of network traffic signature, analysis and
vulnerability scanning are also covered which will help the Network
Administrator design greater network security policies and successful incident
response plans CND
Network Defender Training is for CID Crime Investigation
Department Pakistan, FIA Federal Investigation Agency Pakistan, Pakistan
Security Agencies, Pakistan Army, Pakistan Air Force, Pakistan Navy, Pakistan
Intelligence Department, Cyber Crime Investigation Department, Information Security Organization, Pakistan Defense & Govt.
Security Organization can do CND Certified Network Defender Course in Lahore or
Network Defender CND Training in Pakistan

CSCU Secure Computer User Training Course in Lahore Pakistan. The CSCU
training program aims at equipping the students with the necessary knowledge and
skills to protect their information assets. The program is designed to
interactively teach the students about the whole gamut of information security
threats they face ranging from identity theft and credit card fraud to their
physical safety. The skills acquired during the course of this program will not
only help the students to identify these threats but also to mitigate them
effectively. The purpose of the CSCU training program is to provide individuals with the
necessary knowledge and skills to protect their information assets. This class
will immerse students into an interactive environment where they will acquire a
fundamental understanding of various computer and network security threats such
as identity theft, credit card fraud, online banking phishing scams, virus and
backdoors, emails hoaxes, sex offenders lurking online, loss of confidential
information, hacking attacks and social engineering. More importantly, the
skills learned from the class helps students take the necessary steps to
mitigate their security exposure. The CSCU training program aims at
equipping the students with the necessary knowledge and skills to protect their
information assets. The program is designed to interactively teach the students
about the whole gamut of information security threats they face ranging from
identity theft and credit card fraud to their physical safety. The skills
acquired during the course of this program will not only help the students to
identify these threats but also to mitigate them effectively. CSCU training
Institute in Lahore Pakistan.
Certified Secure Computer User CSCU Training in
Lahore Pakistan

ECIH Incident Handler Training Course in Lahore Pakistan. The EC-Council Certified Incident Handler (ECIH) program is designed to provide the
fundamental skills to handle and respond to the computer security incidents in
an information system. The course addresses various underlying principles and
techniques for detecting and responding to current and emerging computer
security threats. Students will learn how to handle various types of incidents,
risk assessment methodologies, and various laws and policies related to incident
handling. After attending this course, they will be able to create incident
handling and response policies as well as deal with various types of computer
security incidents.
This latest iteration of EC-Council’s Certified Incident Handler (E|CIH) program has been designed and developed in collaboration with cybersecurity and incident handling and response practitioners across the globe. It is a comprehensive specialist-level program that imparts knowledge and skills that organizations need to effectively handle post breach consequences by reducing the impact of the incident, from both a financial and a reputational perspective.
Professionals interested in pursuing incident handling and response as a career require comprehensive training that not only imparts concepts but also allows them to experience real-scenarios.
The E|CIH program includes hands-on learning delivered through labs within the training program. True employability after earning a certification can only be achieved when the core of the curricula maps to and is compliant with government and industry-published incident and response frameworks. E|CIH is a method-driven program that uses a holistic approach to cover vast concepts concerning organizational incident handling and response from preparing and planning the incident handling response process to recovering organizational assets after a security incident. These concepts are essential for handling and responding to security incidents to protect organizations from future threats or attacks.
The Incident Handler ECIH training Institute in
Lahore Pakistan IT incident management training program will enable students to be
proficient in handling and responding to various security incidents such as
network security incidents, malicious code incidents, and insider attack
threats. In addition, students will learn about computer forensics and its role
in handling and responding to incidents. The course also covers incident
response teams, incident management training methods, and incident recovery
techniques in detail. The ECIH certification will provide professionals greater
industry acceptance as the seasoned incident handler. Incident
Handling ECIH Training in Lahore Pakistan

CSA Certified SOC Analyst Training Course in Lahore Pakistan. The Certified
SOC Analyst (CSA) program is the first step to joining a Security
Operations Center (SOC). As the security landscape is expanding, a
SOC team offers high quality IT-security services to actively detect potential
cyber threats/attacks and quickly respond to security incidents. Organizations
need skilled SOC Analysts who can serve as the front-line defenders,
warning other professionals of emerging and present cyber threats. As the security landscape is expanding, a SOC team offers high-quality IT-security services to detect potential cyber threats/attacks actively and quickly respond to security incidents. Organizations need skilled SOC Analysts who can serve as the front-line defenders, warning other professionals of emerging and present cyber threats. Recent
years have witnessed the evolution of cyber risks, creating an unsafe
environment for the players of various sectors.It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entry-level and intermediate-level operations. SOC Analyst training Institute in
Lahore Pakistan.
CSA is a training and credentialing program that helps the candidate acquire trending and in-demand technical skills through instruction by some of the most experienced trainers in the industry.
The program focuses on creating new career opportunities through extensive, meticulous knowledge with enhanced level capabilities for dynamically contributing to a SOC team. it thoroughly covers the fundamentals of SOC operations, before relaying the knowledge of log management and correlation, SIEM deployment, advanced incident detection, and incident response. Additionally, the candidate will learn to manage various SOC processes and collaborate with CSIRT at the time of need. The lab-intensive SOC Analyst training program in Pakistan emphasizes the holistic approach to deliver elementary as well as advanced knowledge of how to identify and validate intrusion attempts. Through this, the candidate will learn to use SIEM solutions and predictive capabilities using threat intelligence. The program also introduces the practical aspect of SIEM using advanced and the most frequently used tools. The candidate will learn to perform enhanced threat detection using the predictive capabilities of Threat Intelligence.SOC Analyst training Institute in
Lahore Pakistan To handle these sophisticated threats, enterprises need advanced
cybersecurity solutions along with traditional methods of defense. Practicing
good cybersecurity hygiene and implementing an appropriate line of defense, and
incorporating a security operations center (SOC) have become reasonable
solutions. The team pursues twenty-four-hour and “follow-the-sun” coverage for
performing security monitoring, security incident management, vulnerability
management, security device management, and network flow monitoring. A
SOC Analyst continuously monitors and detects potential threats, triages the
alerts, and appropriately escalates them. Without a SOC analyst, processes such
as monitoring, detection, analysis, and triaging will lose their effectiveness,
ultimately negatively affecting the organization.
EC-Council Certified SOC Analyst Training in Lahore Pakistan

EDRP Disaster Recovery Training Course in Lahore Pakistan. EDRP course teaches you the methods in identifying vulnerabilities and takes
appropriate countermeasures to prevent and mitigate failure risks for an
organization. It also provides the networking professional with a foundation in
disaster recovery course principles, including preparation of a disaster
recovery plan, assessment of risks in the enterprise, development of policies,
and procedures, and an understanding of the roles and relationships of various
members of an organization, implementation of a plan, and recovering from a
disaster. IT disaster recovery course takes an enterprise-wide approach to
developing a disaster recovery plan. Students will learn how to create a secure
network by putting policies and procedures in place, and how to restore a
network in the event of a disaster. Disaster Recovery EDRP Training Institute in Lahore Pakistan. The EDRP certification is aimed at educating and validating a candidate’s ability to plan, strategize, implement, and maintain a business continuity and disaster recovery plan.
Even scarier is the study that shows that 2 out of 5 business still do not even have a disaster recovery and business continuity plan. And out of the ones that do, only about half of them even test it regularly to see if it is still relevant. Furthermore, industry experts have reiterated the fact in every forum possible, that the size of the business is irrelevant to having a recovery and business continuity plan. Everyone needs to have one to stay relevant in current times. This scenario can only be amended by trained BC/DR professionals who not only understand the gravity of the situation, but also are equipped to ensure that businesses are least impacted when a disaster strikes.
Disaster Recovery Professional EDRP Training in Lahore Pakistan

EC-Council Certified Threat Intelligence Analyst Training in Lahore Pakistan (C|TIA)
is designed and developed in collaboration with cybersecurity and threat
intelligence experts across the globe to help organizations identify and
mitigate business risks by converting unknown internal and external threats into
known threats. It is a comprehensive, specialist-level program that teaches a
structured approach for building effective threat intelligence. In the
ever-changing threat landscape, Student Shelter In Computers Offers Certified
Threat Intelligence Analyst Training Course in Pakistan (C|TIA) is an
essential program for those who deal with cyber threats on a daily basis.
Organizations today demand a professional-level cybersecurity threat
intelligence analyst who can extract the intelligence from data by implementing
various advanced strategies. Such professional-level programs can only be
achieved when the core of the curricula maps with and is compliant to government
and industry published threat intelligence frameworks. C|TIA is a method-driven
program that uses a holistic approach, covering concepts from planning the
threat intelligence project to building a report to disseminating threat
intelligence. These concepts are highly essential while building effective
threat intelligence and, when used properly, can secure organizations from
future threats or attacks.
This program addresses all the stages involved in the Threat Intelligence Life Cycle. This attention to a realistic and
futuristic approach makes C|TIA one of the most comprehensive threat
intelligence certifications on the market today. This program provides the
solid, professional knowledge that is required for a career in threat
intelligence, and enhances your skills as a Threat Intelligence Analyst,
increasing your employability. It is desired by most cybersecurity engineers,
analysts, and professions from around the world and is respected by hiring
authorities. The Purpose of C|TIA is: To enable individuals and organizations with
the ability to prepare and run a threat intelligence program that allows ‘evidence-based knowledge’ and provides ‘actionable advice’ about ‘existing
and unknown threats’. To ensure that organizations have predictive
capabilities rather than just proactive measures beyond active defense
mechanism. To empower information security professionals with the skills to
develop a professional, systematic, and repeatable real-life threat intelligence
program. To differentiate threat intelligence professionals from other
information security professionals. For individuals: To provide an
invaluable ability of structured threat intelligence to enhance skills and boost
their employability. Cyber threat intelligence includes reliable data
collection from numerous sources, context relevant analysis, production of
useful intelligence, and distributing the relevant information to stakeholders.
Organizations can upgrade their defenses and create countermeasures by
acquiring intelligence related to the Tactics, Techniques, and Procedures
(TTPs) of potential threat actors. A threat intelligence analyst
should have specialized skills and knowledge to competently understand the
methodology and mindset of modern attackers and deploy the threat intelligence
accordingly. This program will benefit students who are looking to build
effective threat intelligence for their organization in order to combat
modern-day cyber-attacks and prevent future attacks. CITA Threat Intelligence Analyst
Training in Lahore Pakistan

ECSS Security Specialist Training Course in Lahore Pakistan. EC-Council Certified Security Specialist (ECSS) allows students to enhance their
skills in three different areas namely information security, network security,
and computer forensics. Information security training course in Lahore
Pakistan , plays a vital role in most organizations. Information
security is where information, information processing, and communications are
protected against the confidentiality, integrity, and availability of
information and information processing. In communications, information security
also covers trustworthy authentication of messages that covers identification of
verifying and recording the approval and authorization of information,
non-alteration of data, and the non-repudiation of communication or stored data.
EC-Council Certified Security Specialist (ECSS) is the stage one to the stepping stool of security programs. ECSS Security Specialist Training Course in Lahore covers the basic ideas of data security, PC crime scene investigation and system security individually. This preparation program intends to accommodate a comprehensive methodology with respect to the segments of data security, PC criminology and system security. EC-Council Certified Security Specialist (ECSS) allows students to enhance their skills in three different areas namely information security, network security, and computer forensics.
Information security plays a vital role in most organizations. Information security is where information, information processing, and communications are protected against the confidentiality, integrity, and availability of information and information processing. In communications, information security also covers trustworthy authentication of messages that covers identification of verifying and recording the approval and authorization of information, non-alteration of data, and the non-repudiation of communication or stored data. This preparation program is most appropriate for up-and-comers who need to assemble their vocation in the Cyber security area. ECSS Training Course in Lahore Pakistan.
EC-Council Certified Security
Specialist ECSS Training in Lahore Pakistan

CNDA Network Defense Training Course in Lahore Pakistan. The Certified Network
Defense Architect (CNDA) certification , which has been
designed specially government/military agencies, certifies individuals in the
specific network security discipline of Ethical Hacking from a vendor-neutral
perspective. The CNDA certification will fortify the application knowledge of
security officers, auditors, security professionals, site administrators, and
anyone who is concerned about the integrity of the network infrastructure. A
Certified Network Defense Architect is a skilled professional who understands
and knows how to look for the weaknesses and vulnerabilities. The Certified Network Defense Architect Certification training in Pakistan certification will fortify the application knowledge of security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. A Certified Network Defense Architect Training in Lahore is a skilled professional who understands and knows how to look for the weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker.
Certified Network Defense Architect Certification CNDA Training Course in Pakistan certifies individuals in the specific network security discipline of Network Defense from a vendor-neutral perspective. This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks, no real network is harmed. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Students will also learn about Intrusion Detection, Policy Creation, Social Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student leaves this intensive class they will have hands on understanding and experience in Ethical Hacking.This course prepares you for Certified Network Defense Architect Certified Network Defense
Architect CNDA Training in Lahore Pakistan

ECVP VOIP Training Course in Lahore Pakistan. EC-Council Certified VoIP Professional , Internet and computer technology have
already changed the way people live, work and communicate. VoIP (Voice over
Internet Protocol) is one of the converged technologies behind this
communication revolution. VoIP is a family of technologies that allow IP
networks to be used for voice applications, such as telephony, voice instant
messaging, and teleconferencing. VoIP entails solutions at almost every layer of
an IP network from specialized voice applications (like Skype) all the way down
to low-level quality measures including quality of service (QOS) that keep those
applications running smoothly. VoIP and IP telephony are becoming increasingly
popular with large corporations to consumers alike. Internet Protocol (IP) is
increasingly viewed as more than just a way to transport data, but also as a
tool that simplifies and streamlines a wide range of business applications.
Telephony is the most obvious example. VoIP training course in Lahore or voice over internet protocol
(IP) – is also the foundation for more advanced unified communications
applications that can have an increasingly transformative effect on the way you
do business. Internet and computer technology have already changed the way people live, work and communicate. VoIP Voice over Internet Protocol is one of the converged technologies behind this communication revolution. VoIP and IP telephony are becoming increasingly popular with large corporations to consumers alike. Internet Protocol (IP) is increasingly viewed as more than just a way to transport data, but also as a tool that simplifies and streamlines a wide range of business applications. Telephony is the most obvious example. VoIP – or voice over internet protocol (IP) – is also the foundation for more advanced unified communications applications that can have an increasingly transformative effect on the way you do business. ECVP certification covers VoIP technologies ranging from concepts, implementation to deployment. ECVP Training Institute in Lahore Pakistan.
EC-Council Certified VOIP
Professional ECVP Training in Lahore Pakistan

ECSP Training Course in Lahore Pakistan. Software defects, bugs, and flaws in the logic of a program are consistently the
cause for software vulnerabilities. Analysis by software security professionals
has proven that most vulnerabilities are due to errors in programming. Hence, it
has become crucial for organizations to educate their software developers about
secure coding practices. Attackers scan for security vulnerabilities in
applications and servers and attempt to use these vulnerabilities to steal
secrets, corrupt programs and data, and gain control of computer systems and
networks. Sound programming techniques and best practices should be used to
develop high quality code to prevent web application attacks. Secure programming
is a defensive measure against attacks targeted towards application systems.Learn how to code and develop secure applications with greater stability and posing minimal security risks to the consumer. Get your EC-Council Certified Secure Programmer course in Pakistan. Depending on whether you're used to working with .NET or Java, you'll be able to tailor your course based on the environment you work in. Choose either the .NET or Java labs and exam - and get the accreditation you want. As an ECSP you'll improve the overall quality of your products and applications by identifying security flaws and implementing security countermeasures throughout the software development life cycle. This course is based on the OWASP (Open Web Application Security Project) Top Ten Threats, a guide to the most common categories of application security problems. ECSP Training Institute in Lahore Pakistan.
EC-Council Certified Secure Programmer ECSP Training in Pakistan

ECES Encryption Specialist Training Course in Lahore Pakistan. EC-Council Certified Encryption Specialist (ECES) program introduces
professionals and students to the field of cryptography. Anyone involved in the
selection and implementation of VPN’s or digital certificates should attend this
course. Without understanding the cryptography at some depth, people are limited
to following marketing hype. Understanding the actual cryptography allows you to
know which one to select. A person successfully completing this course will be
able to select the encryption standard that is most beneficial to their
organization and understand how to effectively deploy that technology.
This course is excellent for ethical hackers and penetration testing
professionals as most penetration testing courses skip cryptanalysis completely.
Many penetration testing professionals testing usually don’t attempt to crack
cryptography. A basic knowledge of cryptanalysis is very beneficial to any
penetration testing. This course is excellent for ethical hackers and penetration testing professionals as most penetration testing courses skip cryptanalysis completely. Many penetration testing professionals testing usually don’t attempt to crack cryptography. A basic knowledge of cryptanalysis is very beneficial to any penetration testing.EC-Council Certified Encryption Specialist training in Pakistan, ECES certification and training helps information security professionals to gain far-reaching understanding of cryptography. The training provides understanding of the core concepts of futuristic key and symmetric cryptography along with a detailed understanding of algorithms including DES, AES and Feistel Networks. Candidates also learn about algorithms such as Twofish, Blowfish, and Skipjack, hashing algorithms such as SHA, MD5, MD6, RIPMD 256, Gost, etc. The program also covers the fundamentals of asymmetric cryptography that consists of ElGamal, RSA, DSA, and Elliptic Curve. Eminent concepts like confusion, diffusion, and Kerkchoff’s principle, setting up a VPN, encrypting a drive, implementing steganography and cryptographic algorithms including ciphers such as Caesar cipher, AES and RSA are also explained during this certification training.
EC-Council Certified Encryption
Specialist ECES Training in Lahore Pakistan

ECSP.Net Training Course in Lahore Pakistan. ECSP course will be invaluable to software developers and programmers alike
to code and develop highly secure applications and web applications. This is
done throughout the software life cycle that involves designing, implementing,
and deployment of applications. .Net is widely used by organizations as a
leading framework to build web applications. ECSP.Net teaches developers how to
identify security flaws and implement security countermeasures throughout the
software development life cycle to improve the overall quality of products and
applications. EC-Council Certified Secure Programmer lays the foundation
required by all application developers and development organizations to produce
with greater stability and fewer security risks to the consumer. The Certified
Secure Programmer standardizes the knowledge base for application development by
incorporating the best practices followed by experienced experts in the various
domains.Software defects, bugs, and flaws in the logic of a program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors in programming. Hence, it has become crucial for organizations to educate their software developers about secure coding practices. Attackers scan for security vulnerabilities in applications and servers and attempt to use these vulnerabilities to steal secrets, corrupt programs and data, and gain control of computer systems and networks. Sound programming techniques and best practices should be used to develop high quality code to prevent web application attacks. Secure programming is a defensive measure against attacks targeted towards application systems.ECSP.Net Training Institute in Lahore Pakistan.
EC-Council Certified Secure Programmer ECSP.Net
Training in Lahore Pakistan

CASE.Net Training Course in Lahore Pakistan. ECSP course will be invaluable to software developers and programmers alike
to code and develop highly secure applications and web applications. This is
done throughout the software life cycle that involves designing, implementing,
and deployment of applications. .Net is widely used by organizations as a
leading framework to build web applications. CASE.Net teaches developers how to
identify security flaws and implement security countermeasures throughout the
software development life cycle to improve the overall quality of products and
applications. The .Net framework has increased in popularity because of its open
source nature, interoperability, language independence, It has become the preferred choice of application
developers. However, there are not many training programs that address secure
application development. While .Net developers often learn security on the job,
primarily because the basic education of programming does not usually cover or
emphasize security concerns, the CASE program trains these developers to place
importance on security. The ECSP.Net course will be invaluable to software developers and programmers alike to code and develop highly secure applications and web applications. This is done throughout the software life cycle that involves designing, implementing, and deployment of applications. .Net is widely used by organizations as a leading framework to build web applications. ECSP.Net teaches developers how to identify security flaws and implement security countermeasures throughout the software development life cycle to improve the overall quality of products and applications. CASE.Net Training Institute in Lahore Pakistan.
Certified
Application Security Engineer Cast.Net Training
in Lahore Pakistan
CASE Java Training Course in Lahore Pakistan. CASE Java course will be invaluable to software developers and programmers alike
to code and develop highly secure applications and web applications. This is
done throughout the software life cycle that involves designing, implementing,
and deployment of applications. Java is widely used by organizations as a
leading framework to build web applications. CASE Java teaches developers how to
identify security flaws and implement security countermeasures throughout the SDLC software development life cycle to improve the overall quality of products and
applications. For most organizations, software and applications determine their
success. However, expedition, duplication, and penny-pinching often take centrestage with security consideration taking a backseat or is not present at
all. An insecure or vulnerable application places these businesses at risk.
Addressing security in each phase of the SDLC is the most effective way to
create highly secure applications. Robust security-focused design principles
followed by rigorous security-focused coding, testing, and deployment practices
will lead to applications that can stand up to attacks. This will result in
lower ownership costs for both, the end user and the application vendor. CASE
Java Training Institute in Lahore Pakistan. .Net is widely used by almost all organizations as the leading framework to build web applications. The course teaches developers how to identify security flaws and implement security countermeasures throughout the software development life cycle to improve the overall quality of products and applications. EC-Council Certified Secure Programmer training course in Pakistan lays the foundation required by all application developers and development organizations to produce applications with greater stability and fewer security risks to the consumer. The Certified Secure Application Developer standardizes the knowledge base for application development by incorporating the best practices followed by experienced experts in the various domains. This course is purposefully built with tons of labs peppered throughout the three days of training, offering participants critical hands on time to fully grasp the new techniques and strategies in secure programming.
Certified
Application Security Engineer Cast Java Training
in Lahore Pakistan

CCSIO Chief Information Security Officer Training Course in Lahore Pakistan. CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the foundation of the program and outlining the content that would be covered by the exam, body of knowledge, and training. Some members of the Board contributed as authors, others as exam writers, others as quality assurance checks, and still others as trainers. The Certified CISO (CCISO) program is the first of its kind training and certification program aimed at producing top-level information security executives. The CCISO does not focus solely on technical knowledge but on the application of information security management principles from an executive management point of view. Candidates who do not yet meet the CCISO requirements but are interested in information security management can pursue the Information Security Management (EISM) certification. The recent increase in security breaches has caused many organizations to put a greater emphasis on improving the skills of the information security (IS) workforce. Research shows IS certifications lead to improved job performance and higher returns on investment. Chief Information Security Officer Certification in Pakistan (C|CISO) equips CISOs with the most effective toolset to lead a high performing information security program and defend the company from cyber attacks.
Chief Information Security Officer CCSIO Training Institute in Lahore “CISO is a unique designation that has been designed in cooperation with industry leaders to identify a solid blend of functional and executive IT job roles and skill requirements”Chief Information Security Officer Certification in Pakistan prepares Chief Information Security Officers (CISOs) to defend their organizations from security breaches by actively improving the current information technology security solutions, enforcing regulatory requirements and aligning IS with the strategic needs and goals of their organization. This skill set enables the CISO to be the best guardian of their organization’s digital assets. C|CISO is the first certification of its kind to equip Information Assurance leaders with the most effective toolset to defend organizations from cyber attacks. It recognizes an individual’s accumulated skills in developing and executing an information security management strategy in alignment with organization goals. Cyber attacks across the world are increasing in both frequency and intensity, says information security expert Such attacks are able to cripple organizations in a single blow, a consequence that cannot be ignored by any business strategy due to the lack of protection afforded by current legal framework. The Certified CISO (C|CISO) course has certified leading information security professionals around the world and is the first of its kind training and certification program aimed at producing top-level Information Security Leaders. The CCISO does not focus solely on technical knowledge but on the application of information security management principles from an executive management point of view. The program was developed by seasoned CISOs for current and aspiring CISOs. Chief Information Security Officer CISO Training Course in Lahore Pakistan
C|CISO Material assumes a high-level understanding of technical topics and doesn’t spend much time on strictly technical information, but rather on the application of technical knowledge to an information security executive’s day-to-day work. The C|CISO aims to bridge the gap between the executive management knowledge that CISOs need and the technical knowledge that many aspiring CISOs have. This can be a crucial gap as a practitioner endeavors to move from mid-management to upper, executive management roles. Much of this is traditionally learned as on the job training, but the C|CISO Training Program can be the key to a successful transition to the highest ranks of information security management. To sit for the (CCISO) exam after taking training, candidates must have five years of experience in three of the five CCISO domains: (1) Governance, (2) Security Risk Management, Controls, & Audit Management, (3) Security Program Management & Operations, (4) Information Security Core Concepts, and (5) Strategic Planning, Finance, & Vendor Management. Certified Chief Information Security Officer CCISO Training Course in Lahore Pakistan

EC-Council ENSA Network Security Administrator Training in Lahore Pakistan , (ENSA) certification verifies candidate’s network security skills and knowledge from defensive perspective while the CEH certification looks at the security from an offensive view. An ENSA should have fundamental skills to analyze the internal and external security threats against a network, and to develop security policies that will protect an organization’s information. Certified professionals should know how to evaluate network and Internet security issues and design, and how to implement successful security policies and firewall strategies. In addition, they should know how to expose system and network vulnerabilities and defend against them. This course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop security policies that will protect an organization’s information. Students will learn how to evaluate network and Internet security issues and design, and how to implement successful security policies and firewall strategies. In addition, they will learn how to expose system and network vulnerabilities and defend against them. Becoming a Network administrator is a good career choice if you are looking to start a rewarding career or if you like handling both software and hardware; and if you understand how computers work. Network administrators spend lots of time with network environments and are familiar with network components, traffic, performance and utilization, network topology, location of each system, network security measures, etc. Organizations can improve their defense against cyberattacks when their IT experts and network administrators are equipped with adequate network security skills.
Network Administrator training course in Pakistan plays a crucial function in supervising and maintaining an organization’s
technological network. They work within governmental agencies and private
organizations to supervise network segments, wide area networks, local area
networks, and other related network systems. They also manage the information
technology within the association, functioning as the go-to professionals for
critical technical or computer-based issues. A network administrator’s job
description may vary from one organization to the next, but on-site servers,
software-network interactions, as well as network integrity/resilience are the
key areas of focus. Likewise, the role of a network admin slightly differs from
that of a system administrator even though they are sometimes used
interchangeably. Nevertheless, their differences are most noticeable based on
their work environments and in larger organizations. Any organization that utilizes several computers or software platforms requires the services of a network systems administrator to manage and link the various systems. As organizations continue to expand, their networks and systems also become larger and more multifaceted.
All these increase the demand for people with network defense skills to support the available systems. Moreover, owing to the increase in cyber-breaches and attacks, organizations are beginning to focus their efforts on cyber defense solutions. Even with best practices, several organizational networks are still being compromised. This is why it’s a good time to be a network administrator. Organizations need skilled or certified network defenders who are proficient at detecting, protecting, and responding to threats within a network. With the rise in the global economy, organizations are implementing advanced systems for operations and data storage. Demand for network administrators is expected to increase due to the rising demand for information security. Companies will look forward to hiring network administrators for optimizing their systems, to lower costs, and to increase their productivity. Since a large number of industries are currently deeply computer-supported, most organizations need network administrators. Network administrators are responsible for the daily operations and security of computers and networks. The network admin has a broad range of responsibilities. They are responsible for the general operations of the organization’s technical networks, they support several IT teams, and they fix and prevent network issues.
Network Security Administrator Training Course in Lahore Pakistan



Designed &
Developed by Webmaster Abbas Shahid Baqir
Webmaster Feedback:
stscomps@yahoo.com
All Rights
Reserved Copyright, 2010-2035 Student Shelter In Computers
®